Thycotic Secret Server
- Thycotic Secret Server Architecture
- Thycotic Secret Server Manual
- Thycotic Secret Server Mfa
- Thycotic Secret Server Pricing
Important
The Thycotic Secret Server connector is currently in PREVIEW. See the Supplemental Terms of Use for Microsoft Azure Previews for additional legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
The Thycotic Password Filler extension for Secret Server has been built with a new modern look and feel and provides secure access to your web based Secrets. This extension requires use and integration with Secret Server version 10.7.52 and later. Thycotic’s Secret Server PAM integration with SailPoint IdentityIQ allows organizations to tie Secret Server entitlements back to identities in IdentityIQ. Leveraging the system for cross-domain identity management (SCIM) standard, Thycotic’s SCIM Connector allows the automation and interoperability of user access. Are you a Thycotic Secret Server cloud client and have concerns about your data? I hear this from people all the time. If this is something you are concerned about hit me up and I will put you in contact with a PS team that offers a few different backup options for your data. Thycotic Secret Server Secret Server can integrate with ServiceNow’s incident and Change Management products. This integration includes validating ticket numbers, their status, and adding work detail items to the request.
This article explains how to connect your Thycotic Secret Server appliance to Azure Sentinel. The Thycotic Secret Server data connector allows you to easily connect your Thycotic Secret Server logs with Azure Sentinel, so that you can view the data in workbooks, use it to create custom alerts, and incorporate it to improve investigation. Integration between Thycotic and Azure Sentinel makes use of the CEF Data Connector to properly parse and display Secret Server Syslog messages.
Note
Data will be stored in the geographic location of the workspace on which you are running Azure Sentinel.
Prerequisites
Sketchup 2013 for mac os. You must have read and write permissions on your Azure Sentinel workspace.
You must have read permissions to shared keys for the workspace.
Your Thycotic Secret Server must be configured to export logs via Syslog. Plants vs zombie 2 for mac download.
On your local Windows 10 PC: In the search box on the taskbar, type Remote Desktop Connection. Use the Microsoft Remote Desktop app to connect to a remote PC or virtual apps and desktops made available by your admin. The app helps you be productive no matter where you are. Getting Started Configure your PC for remote access first. Windows home remote desktop app.
Send Thycotic Secret Server logs to Azure Sentinel

To get its logs into Azure Sentinel, configure your Thycotic Secret Server to send Syslog messages in CEF format to your Linux-based log forwarding server (running rsyslog or syslog-ng). This server will have the Log Analytics agent installed on it, and the agent forwards the logs to your Azure Sentinel workspace.
In the Azure Sentinel navigation menu, select Data connectors.
From the Data connectors gallery, select Thycotic Secret Server (Preview), and then Open connector page.
Follow the instructions in the Instructions tab, under Configuration:
Under 1. Linux Syslog agent configuration - Do this step if you don't already have a log forwarder running, or if you need another one. See STEP 1: Deploy the log forwarder in the Azure Sentinel documentation for more detailed instructions and explanation.
Under 2. Forward Common Event Format (CEF) logs to Syslog agent - Follow Thycotic's instructions to configure Secret Server. This configuration should include the following elements:
- Log destination – the hostname and/or IP address of your log forwarding server
- Protocol and port – TCP 514 (if recommended otherwise, be sure to make the parallel change in the syslog daemon on your log forwarding server)
- Log format – CEF
- Log types – all available
Under 3. Validate connection - Verify data ingestion by copying the command on the connector page and running it on your log forwarder. See STEP 3: Validate connectivity in the Azure Sentinel documentation for more detailed instructions and explanation.
It may take up to 20 minutes until your logs start to appear in Log Analytics.
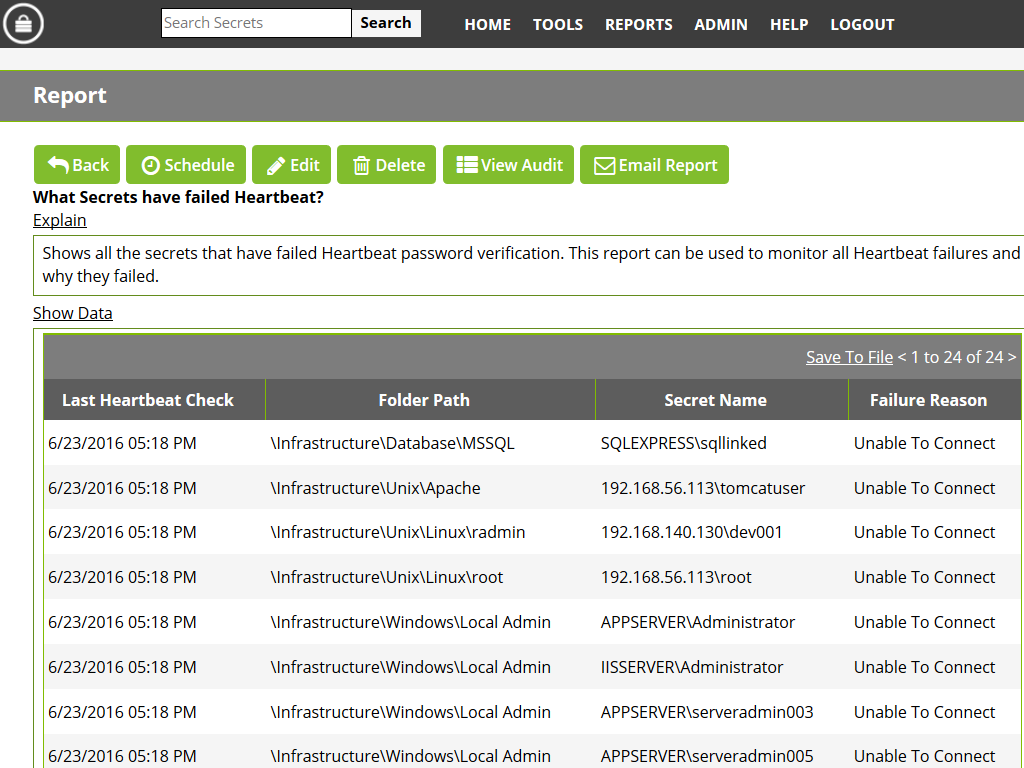
Find your data
After a successful connection is established, the data appears in Logs, under the Azure Sentinel section, in the CommonSecurityLog table.
To query Thycotic Secret Server data in Log Analytics, copy the following into the query window, applying other filters as you choose:
See the Next steps tab in the connector page for some useful workbooks and query samples.
Next steps

In this document, you learned how to connect Thycotic Secret Server to Azure Sentinel. To learn more about Azure Sentinel, see the following articles:
- Learn how to get visibility into your data, and potential threats.
- Get started detecting threats with Azure Sentinel.
- Use workbooks to monitor your data.
Secure Credentialed Scanning
Integration Benefits
- Prevent credential-based attacks without compromising risk visibility
- Improve operational efficiency through automated importation of credentials
- Minimize false positives and increase accuracy by using trusted credentials
Abuse of privileged accounts through compromised credentials is proving to be an increasingly popular tactic for hackers and malicious insiders. When it comes to vulnerability scanning, credentialed scans are more effective because they have a greater reach into an organization’s network.
Integrating Rapid7’s leading vulnerability management solution, InsightVM, or our top-rated on-premise solution, Nexpose, with Thycotic’s SecretServer helps enhance your team’s ability to perform these scans. SecretServer is designed to randomize and store the passwords for accounts on target systems on a regular recurring basis. The passwords are stored and managed by the vault and can be retrieved via a SOAP web service which allows them to be securely shared with other technologies. This integration minimizes the exposure of your critical credentials to possible attackers while allowing your security team to perform critical security assessments.
How It Works
Thycotic’s SecretServer will store and randomize the passwords regularly. As they are needed for a vulnerability scan, the randomized passwords can then be applied to the relevant assets to allow InsightVM* to run a credentialed scan.
Thycotic Secret Server Architecture
Through this integration, joint Rapid7 and Thycotic customers are now able to maximize their efficiency and reduce their risk exposure by utilizing randomized passwords when running credentialed vulnerability scans.
Overview of Integration Process

- Step 1: Create privileged account stores in SecretServer
- Step 2: Create site(s) in InsightVM (or Nexpose) with assets
- Step 3: Install Thycotic’s Password Java SDK
- Step 4: Configure the solution
Thycotic Secret Server Manual
Once the script is deployed, InsightVM will automatically pull the relevant credentials from SecretServer, allowing users to perform scans with an increased level of password security.
What You Need
- Rapid7 InsightVM or Rapid7 Nexpose
- Thycotic SecretServer
Thycotic Secret Server Mfa
Figure 1: SecretServer securely stores your passwords for use in InsightVM or Nexpose
Thycotic Secret Server Pricing
*All mentions of Rapid7 InsightVM associated with the Thycotic SecretServer also apply to Rapid7 Nexpose.
